One second to learn how to protect your system with NFC
In today’s world, safety has become a top priority for everyone, especially for design engineers. Most people don’t realize that they enter up to 20 six-digit passwords or use their fingerprints on their mobile phones daily, and they also input various app passwords around 20 times a day. When designing a new device, it's crucial to implement access protection. For instance, if I were working on a major industrial control system, I would want to enhance access control, track who changes settings on the device, and ensure security for test equipment, vending machines, consumer wearables, and access zones—many of which can be easily secured with NFC technology.
Figure 1: Partial application of Near Field Communication (NFC)
NFC offers great convenience and is built upon RFID technology, enabling two-way wireless communication at high data transfer rates (up to 424 kbps). However, its reading distance is much shorter—between 4 to 10 cm—which enhances security by limiting the range of interaction. There is also an ISO 15693 standard for longer read distances, typically up to 1 meter, often using larger antennas.
One of the most well-known applications of NFC is in the next generation of credit cards, allowing users to complete payments simply by tapping the card near a reader. The shift from magnetic stripe cards to chip-based cards in the US was slow and frustrating, while Europe and South America have been using more secure chip cards for years. However, with over 13,000 financial institutions in the US needing to agree on standards, adoption has been slower than expected.
Currently, the chip cards used in the US require physical contact between the card and the reader. EMV (Europay, Mastercard, Visa) is the global standard for secure authentication chips. These EMV-compliant cards have significantly reduced fraud losses for physical merchants. In 2017, credit card fraud losses dropped by nearly 28% to $3.9 billion, but online fraud remains a challenge.
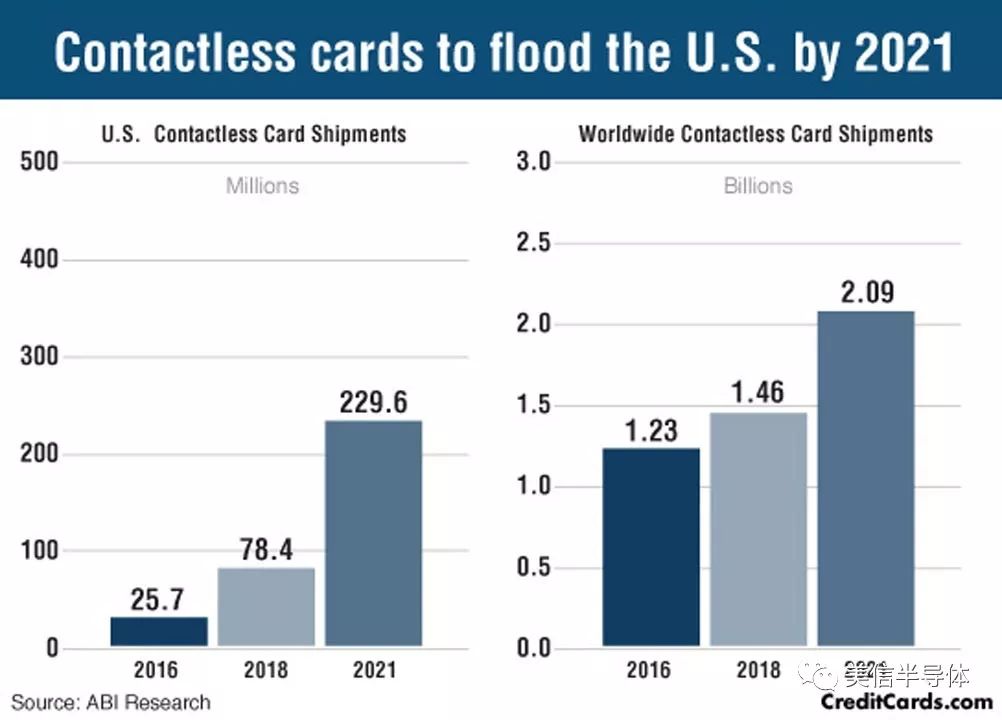
Figure 2: The new flash payment contactless credit card will be launched soon
The EMV standard also applies to next-generation credit cards that support NFC. Many people now use their smartphones for retail payments, and soon, traditional credit cards will also adopt NFC for fast, secure transactions.
NFC Specifications
ISO/IEC 14443 is an international standard for contactless smart cards operating at 13.56 MHz, typically within a 4 cm range. It outlines modulation and transmission protocols and is commonly used for access control and security certifications. ISO/IEC 18000-3 is a broader RFID specification. While you may not need to dive into the technical details yourself, many IC manufacturers offer ready-to-use solutions that simplify implementation.
Working Principle
NFC operates by having the reader generate a 13.56 MHz RF field and poll nearby devices. Once a tag detects a device in the field, it enters "listen" mode. The reader then identifies the type of signal technology the tag uses (NFC-A, NFC-B, or NFC-F), and communication is established based on modulation methods, bit-level coding, and other parameters.
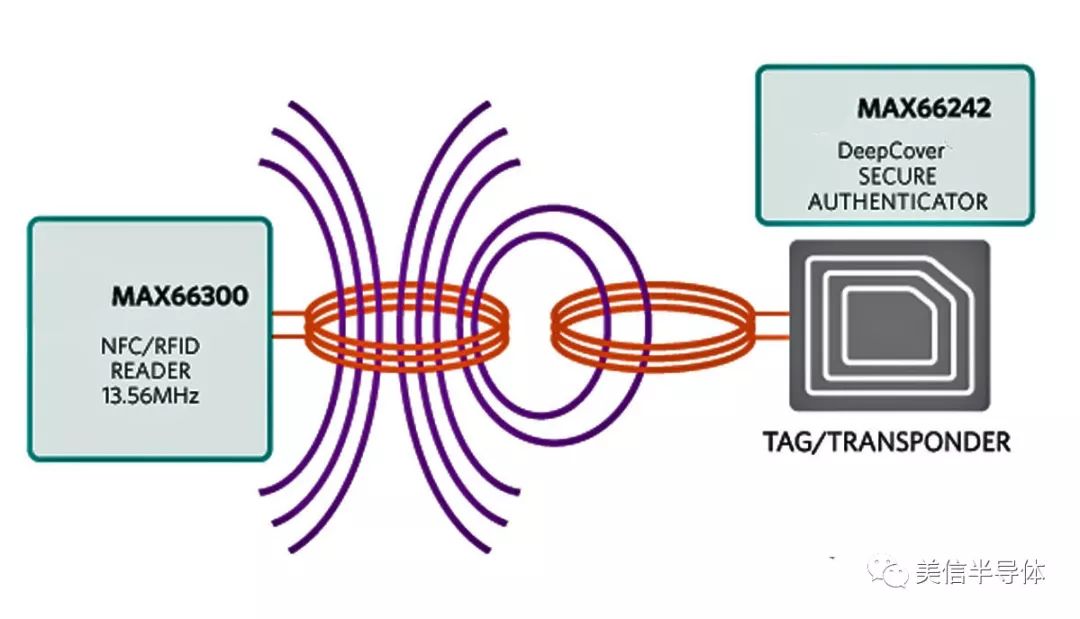
Figure 3: Basic NFC connection
Available Chips
The MAX66242 DeepCover® Secure Authenticator is a transponder IC that integrates an ISO/IEC 15693 and ISO 18000-3 Mode 1 compliant RF front end, an I2C interface, a FIPS 180-based SHA-256 engine, and a 4096-bit user EEPROM. It supports symmetric challenge-response authentication and is powered automatically by the HF RF field. With up to 5mA current output, it ensures a strong field strength.
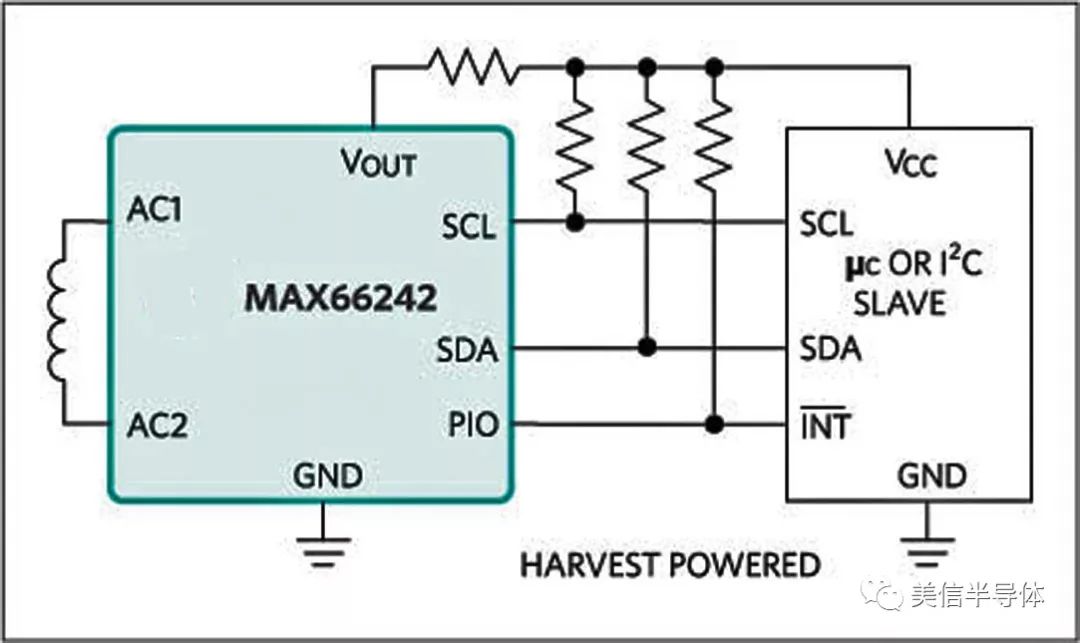
Figure 4: The MAX66242 DeepCover Secure Authenticator Transponder collects data from sensors via I2C
Each device comes with a factory-programmed unique 64-bit ID. It can collect data from connected sensors and transmit it through the RF port. Operating on a 3.3V supply and functioning between -20°C and 85°C, it provides ±8kV HBM ESD protection.
Maxim also offers the MAX66300 DeepCover Contactless Host Security Authenticator, which includes an RFID transceiver and a SHA-256 Secure Authenticator coprocessor. It provides four pages of 32-byte user memory, four master keys, multiple programmable protections, 76-byte SRAM, a hardware true random number generator, and a unique 64-bit serial number.
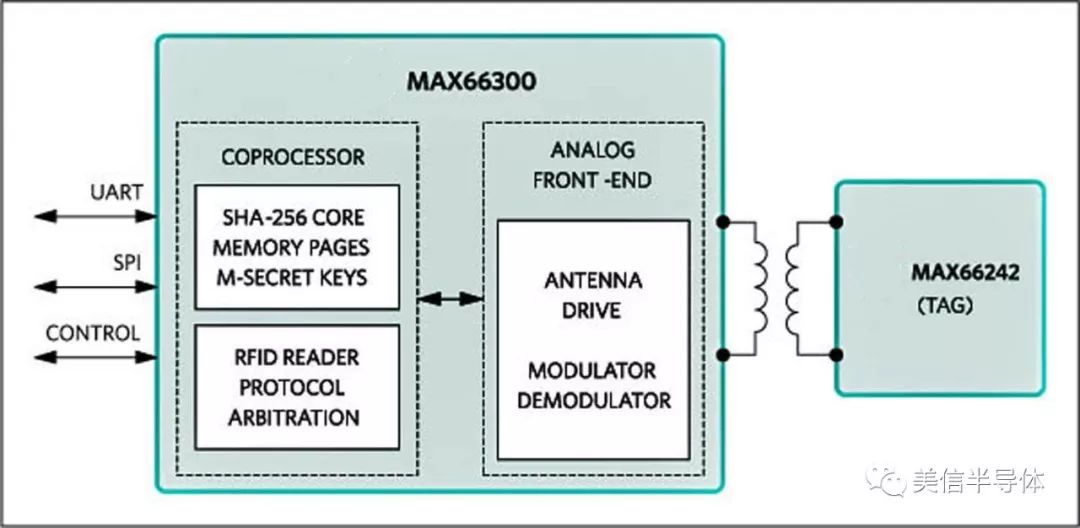
Figure 5: The MAX66300 DeepCover Contactless Host Security Authenticator polls data from tags
The MAX66300 has an RF power output of up to 200mW, adjustable ASK uplink modulation from 7% to 30%, optional low-pass and high-pass filters, and selectable receive gain from 0dB to 40dB. It supports single or dual antenna modes with OOK modulation, operates in a TQFN56 package, and is compatible with -40°C to 85°C temperatures. It features antenna short-circuit protection, a 3.3V or 5V supply, and ±2kV HBM ESD protection on the antenna connection.
Additionally, evaluation kits like the MAX66300-24XEVKIT and MAX66242EVKIT make it easier to prototype and test your designs. Maxim also offers several versions of DeepCover Secure Microcontrollers, such as the MAX32560, which is an Arm Cortex-M3-based SoC with advanced security features, including AES encryption, secure boot, and tamper detection.
Adding NFC security to any design is a straightforward and effective way to enhance customer safety and drive business success.
Wuxi Ark Technology Electronic Co.,Ltd. , https://www.arkledcn.com