One second to learn how to protect your system with NFC
In today's world, where security is more important than ever, especially for design engineers, we often overlook the number of passwords and biometric logins we use daily. On average, each person might enter up to 20 six-digit passwords or fingerprint scans on their mobile devices every day, along with numerous app passwords. When designing a new device—whether it's industrial control systems, testing equipment, vending machines, wearable tech, or access control systems—it's crucial to implement proper access protection. For example, if I were working on an industrial control system, I would want to track who made changes to settings, ensuring transparency and security at every step.
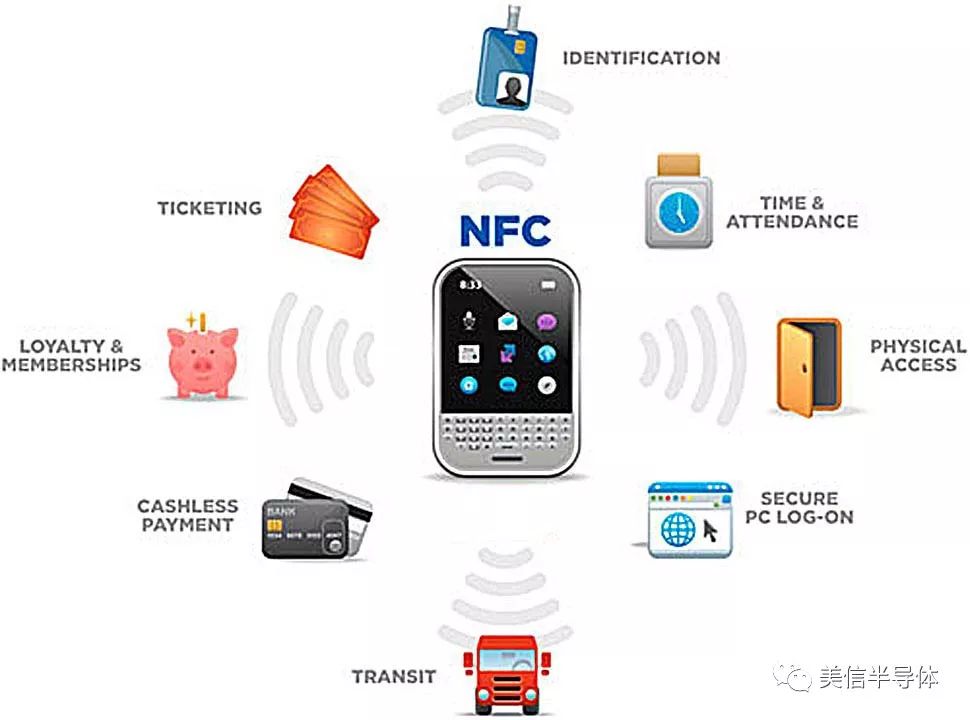
Figure 1: Partial application of Near Field Communication (NFC)
One of the most convenient technologies for secure communication is NFC. It builds upon RFID technology, enabling two-way wireless communication with high data transfer rates (up to 424 kbps), but with a shorter read range—typically between 4 to 10 cm. This limited distance actually enhances security, as it reduces the risk of unauthorized access. There are also standards like ISO 15693 that support longer read distances, up to 1 meter, usually with larger antennas.
A growing area of NFC application is in the next generation of credit cards. These cards allow users to make payments by simply tapping them on a reader. The shift from magnetic stripe cards to chip-based cards in the U.S. was slow, while Europe and South America had already adopted this more secure method years ago. However, with over 13,000 financial institutions needing to agree on the transition, the adoption rate in the U.S. has been slower.
Current chip cards in the U.S. require physical contact between the card and the reader. EMV (Europay, Mastercard, Visa) is the global standard for secure authentication chips. These EMV-compliant cards have significantly reduced in-store fraud, with losses dropping nearly 28% in 2017. But online fraud remains a challenge, which is why the next evolution—NFC-enabled cards—is gaining momentum.
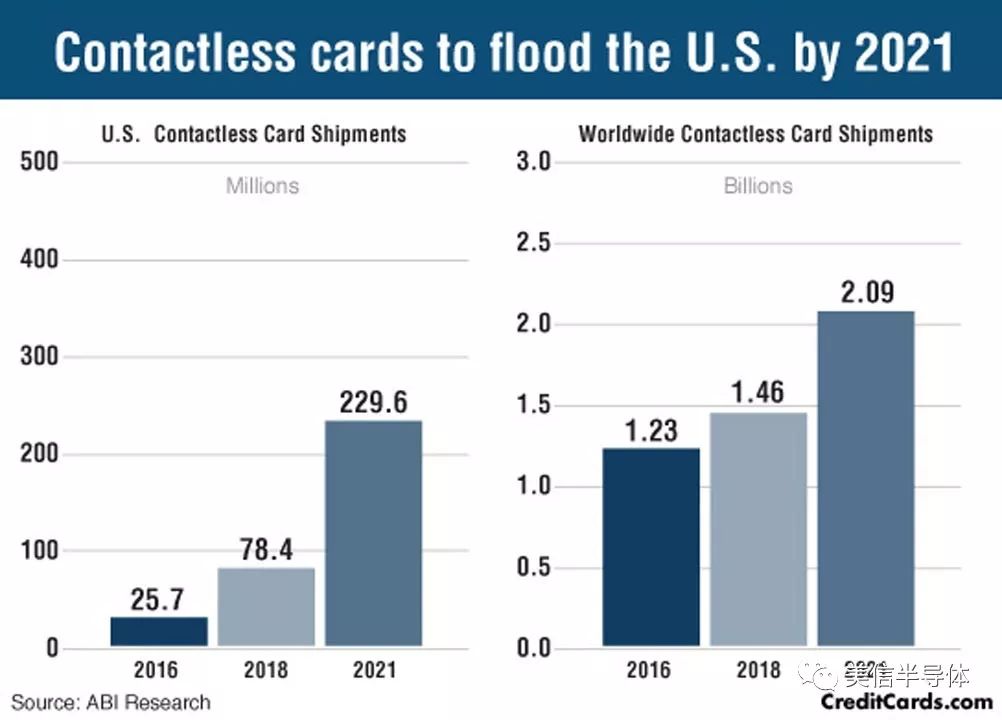
Figure 2: The new flash payment contactless credit card will be launched soon
As more people use NFC on their smartphones for retail payments, credit cards are following suit. NFC technology offers a faster and more secure way to complete transactions, making it a natural next step in payment innovation.
Understanding NFC specifications can help you integrate it into your designs. ISO/IEC 14443 outlines the protocols for contactless smart cards operating at 13.56 MHz, commonly used in access control and security applications. Meanwhile, ISO/IEC 18000-3 covers broader RFID standards. While these specifications are useful, many IC manufacturers provide ready-to-use solutions, making it easier for designers to implement NFC without deep technical knowledge.
How does NFC work? On the reader side, an RF field at 13.56 MHz is generated, and it polls nearby devices. Once a tag detects another device within range, it enters "listen" mode. The reader then identifies the type of signal (NFC-A, NFC-B, or NFC-F) used by the tag and establishes a communication link using specific modulation and coding methods.
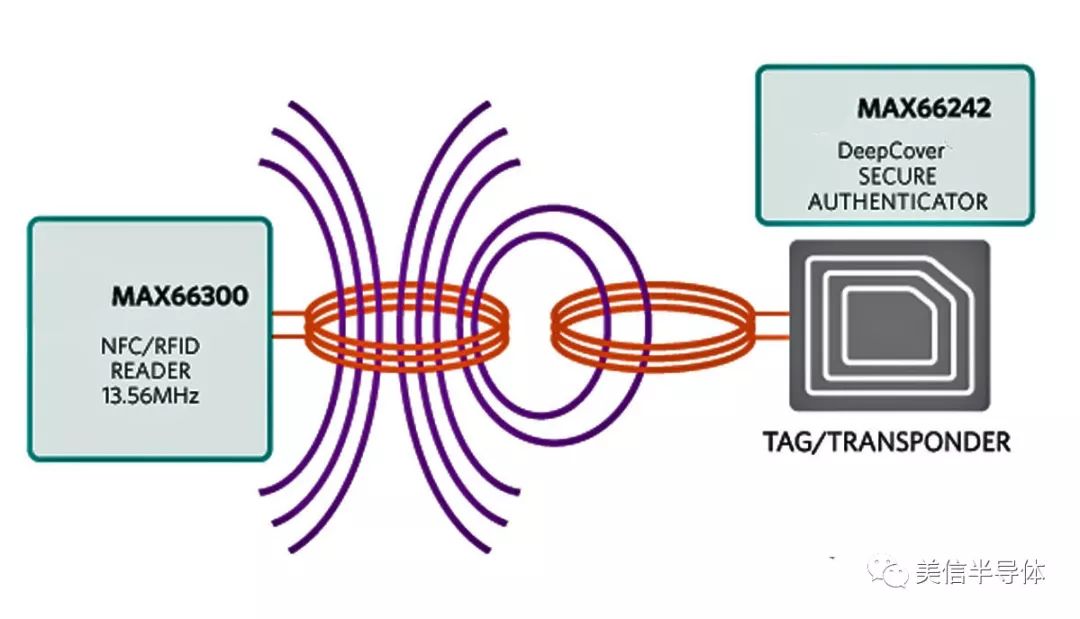
Figure 3: Basic NFC connection
For hardware integration, Maxim Integrated offers several NFC-enabled chips. The MAX66242 DeepCover® Secure Authenticator is one such device. It includes an RF front end compliant with ISO/IEC 15693 and ISO 18000-3 Mode 1, along with an I2C interface, SHA-256 engine, and user EEPROM. This chip provides secure authentication and can collect sensor data via I2C, making it ideal for embedded applications.
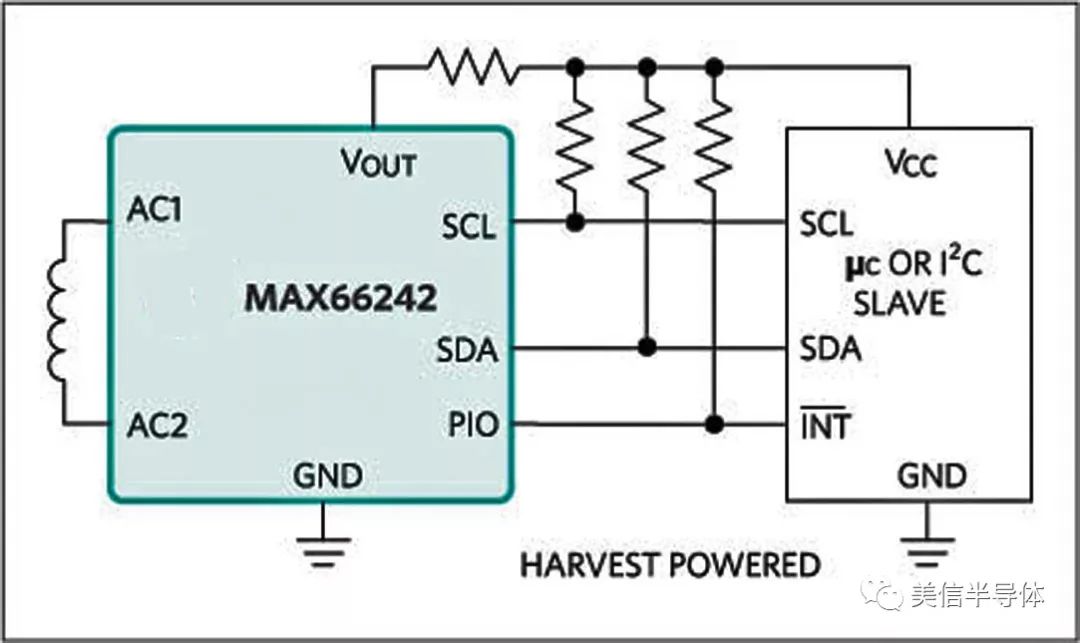
Figure 4: The MAX66242 DeepCover Secure Authenticator Transponder collects data from sensors via I2C
Each device comes with a factory-programmed unique 64-bit ID, ensuring authenticity. The chip can also gather data from connected peripherals and transmit it wirelessly. It operates at 3.3V, with a wide temperature range and robust ESD protection, making it suitable for various environments.
Another option is the MAX66300 DeepCover Contactless Host Security Authenticator, which integrates an RFID transceiver and a SHA-256 coprocessor. It offers four pages of user memory, multiple key options, and advanced security features, including a true random number generator and tamper detection sensors.
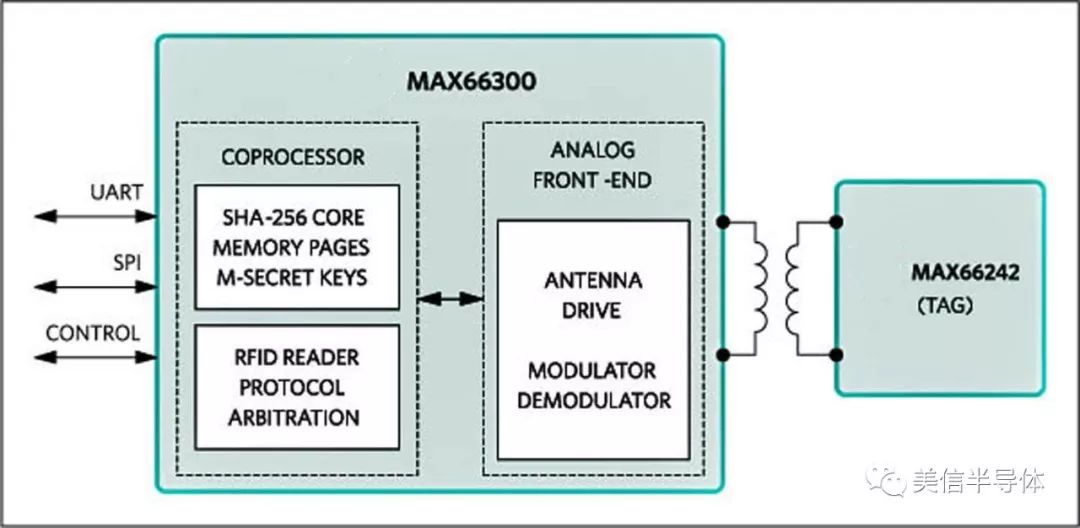
Figure 5: The MAX66300 DeepCover Contactless Host Security Authenticator polls data from tags
With its adjustable RF power output and flexible modulation options, the MAX66300 is designed for a variety of applications. It supports both single and dual antenna modes and includes built-in ESD protection, making it a reliable choice for secure NFC implementations.
Additionally, evaluation kits like the MAX66300-24XEVKIT and MAX66242EVKIT simplify the development process. These tools help designers test and refine their NFC-based systems efficiently.
Maxim also offers other DeepCover Secure Microcontrollers, such as the MAX32560, which combines an Arm Cortex-M3 core with advanced security features, including AES encryption, secure boot, and tamper-resistant sensors. This makes it ideal for applications requiring high levels of security and reliability.
Adding NFC security to your design not only enhances customer safety but also strengthens your product’s market position. With the right components and tools, integrating NFC is a straightforward and effective way to improve both performance and trust in your systems.
Wuxi Ark Technology Electronic Co.,Ltd. , https://www.arkledcn.com