The latest security certification solution based on the working principle of SHA-256 security authentication
In the past decade, SHA-1 security certification has played a crucial role in combating counterfeiting and protecting intellectual property from unauthorized access. As computing power continues to grow, users are increasingly demanding more robust and advanced security solutions.
To meet this growing need, Maxim Integrated introduced a new line of SHA-256 security authenticators along with supporting security coprocessors. This product family provides strong physical security at a low cost, offering protection against IP theft, cloning, and peripheral authentication. This article explores the working principle of SHA-256-based security authentication and highlights the two-way authentication mechanism used in the system.
**Security Certification System**
Implementing a secure authentication system typically involves connecting a sensor or peripheral module to the host system. The system shown in Figure 1 includes a 1-Wire SHA-256 secure authenticator and a SHA-256 coprocessor that also functions as a 1-Wire master. Communication between the host and peripherals occurs through a single pin on the 1-Wire interface, which simplifies design, reduces complexity, and lowers costs.
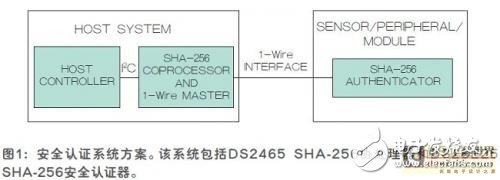
**SHA-256 Security Certification**
The system's SHA-256 authentication supports 256-bit challenges using a 256-bit key. The secure authenticator depicted in Figure 1 is a 1-Wire slave device featuring a unique 64-bit ROM ID, which serves as the foundation for secure authentication calculations. System designers can partition the authenticator’s EEPROM into public (unprotected) and protected areas, where the host must authenticate itself securely. Table 1 outlines the available protection modes and combinations.

*SHA-256 coprocessor with built-in 1-Wire host*
The SHA-256 coprocessor shown in Figure 1 operates as an I2C slave controlled by the host processor. From the host’s perspective, it acts as a 256-byte read/write memory, with specific regions designated for special functions.
**Security Logic**
SHA-based security relies on a message authentication code (MAC) generated from public data and secret keys. To ensure secure authentication, both the host/coprocessor and the 1-Wire secure authenticator must share a "never-leak" key. For maximum security, each 1-Wire Secure Authenticator should have a unique key. This way, if one key is compromised, the entire system remains unaffected.
At first glance, achieving this might seem challenging. However, we’ve implemented a simple yet effective solution: using “data sources†to compute the key, which is then embedded within the device in a trusted production environment. These data sources include the master key, binding data, sub-key, the authenticator’s ROM ID, and other formatted symbols. The process is illustrated in Figure 2.
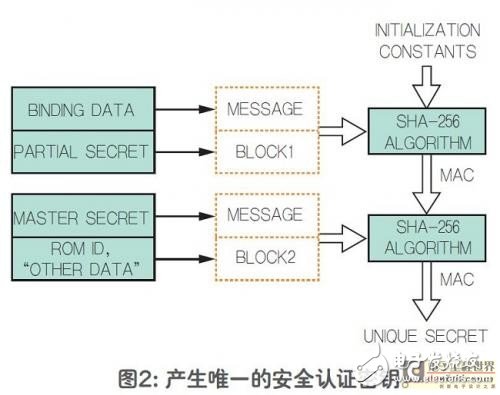
For security and storage reasons, the unique keys of all secure authenticators should not be stored in the coprocessor or host. Instead, the coprocessor only stores the master key and binding data in its protected memory section. The split key is a system constant that can be encoded and shared publicly through the host’s firmware. Once the coprocessor reads the authenticator’s ROM ID, it can compute the unique key, as shown in Figure 2. With this shared key, the secure authenticator and coprocessor can communicate securely, ensuring the integrity and authenticity of the system.
Beam Splitter,Dichroic Beam Splitter,Optical Beam Splitter Cube,Beam Splitter Cube
Danyang Horse Optical Co., Ltd , https://www.dyhorseoptical.com