Android platform mobile phone security system security solution
introduction
Android is a Linux-based open source mobile operating system developed by Google. The platform is composed of operating system, middleware, user interface and application software. It is regarded as the first complete, open and free mobile platform. Due to the continuous development of 3G technology and the advantages of the Android platform, Android mobile application development has become one of the hottest technologies, and the number of smart phones based on the Android platform is also increasing. Due to the convenience and practicability of Android phones, many people will store personal information such as bank card passwords, phone passwords, online payment passwords, important agenda reminders and some private data in their mobile phones. If the mobile phone is stolen, not only privacy leaks such as text messages, address books, photos, etc., but also the deception of relatives and friends may have a great impact on people's work and life.
In order to solve this problem, this paper proposes to monitor whether the mobile phone SIM card is replaced by the anti-theft tracking module after the mobile phone is stolen, so as to determine whether the mobile phone is stolen. And use the instant messaging module to send remote control commands to the stolen mobile phone to protect personal privacy and track the stolen mobile phone. After the phone is locked, the phone can not be used by blocking the button of the phone, intercepting the phone and text message, and turning off the USB debugging connection of the phone, unless unlocked. The system organically combines modules such as anti-theft tracking, instant communication and remote control, and has good research value and application prospects.
1 system overall design
The mobile phone anti-theft system uses the mobile phone terminal as a carrier to realize remote control by means of the GPRS data connection service or the mobile WiFi network and the short message service provided by the communication carrier. Before implementing remote control, the user first needs to start and run the server according to the configured network environment through the GPRS data connection or the mobile WiFi network, and then according to the IP address and port number of the startup server, and the configured user name and password on the server. , activate the client software installed on the Android terminal. After the mobile client software is activated, the cloud server establishes a reliable communication connection with the mobile client; after the connection is successfully established, the user can implement data communication between the server and the client according to the communication protocol of the mobile cloud platform. . The mobile client will need to upload the data or the business data generated by the operation, and package it into a fixed Java Bean packet format and send it to the cloud server, or the cloud server encapsulates the command field sent by the webpage side into a Java Bean packet. The form is then sent to the mobile terminal. The mobile terminal parses the received data packet, and simultaneously completes the corresponding command operation on the mobile phone, and then returns the result of the processing.
Through the analysis of the whole system, starting from the overall architecture of the system, the various functional modules are divided, and the connections between the modules of the system are clarified. By analyzing the characteristics of the C/S mode and the B/S mode, combined with the actual needs of the system, the combination of the C/S mode and the B/S mode is adopted, and the user can not only control the stolen mobile phone through the security number. In an emergency, you can also log in to the mobile phone anti-theft management system on the web to remotely control the stolen mobile phone. The first time to conduct a full-scale monitoring of the stolen mobile phone, so that the thief can not perform any operation on the mobile phone, both protecting the privacy data, and gaining valuable time for retrieving the mobile phone. You can also use GPS location to get the current location of the stolen phone and retrieve the stolen phone as soon as possible. The overall architecture of the system is shown in Figure 1.
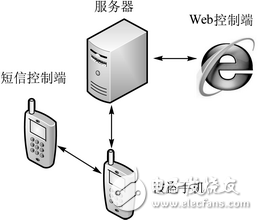
Figure 1 system overall architecture
Figure 1 illustrates the architecture design of the entire system. After the mobile phone is stolen, the user can control the stolen mobile phone through the secure number mobile phone, and can also log in to the mobile phone anti-theft management system on the web through the browser of the PC, and the instant communication module is used. The stolen mobile phone sends a remote control command to perform functions such as mobile phone alarm, data deletion, locking the mobile phone, and GPS positioning. When the stolen mobile phone receives these instructions, it will also perform corresponding processing. After completion, the processing result will be sent to the web terminal through the instant communication module and displayed. Both of these control methods are carried out in secret in the background, and the thief will not have any awareness to track the phone more securely and reliably.
2 anti-theft tracking module design and implementation
The anti-theft tracking module monitors whether the SIM card inserted in the mobile phone is legal by monitoring the boot broadcast of the mobile phone. If it is legal, no processing is performed; otherwise, the SIM card number of the new card is obtained, and the SIM card number is sent as the content of the short message. The mobile phone that specifies the security number to the user, so that the user can obtain the SIM card number of the stolen mobile phone and remotely control the mobile phone. At the same time, the service of forwarding new text messages of stolen mobile phones will be opened. The specific functions of this module are explained below. The anti-theft tracking module processing flow is shown in Figure 2.
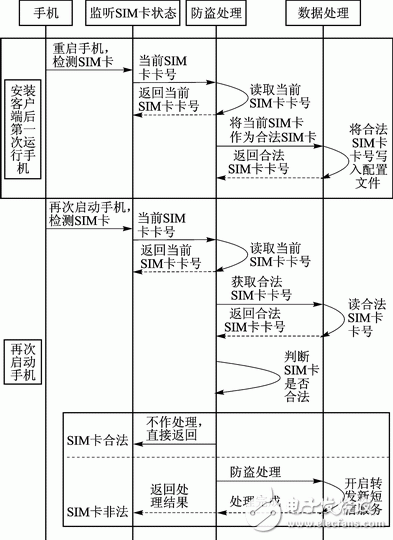
Figure 2 anti-theft tracking module processing flow
1Set and modify the legal SIM card number: When the program is first started, the system will automatically read the SIM card number of the current mobile phone, and write the card number as a valid SIM card number to the automatically generated configuration file. in. Since each SIM card number (ie IMSI serial number) is unique, the card number will be used as the main basis for judging whether the SIM card inserted in the mobile phone is legal. It also allows the user to modify the SIM card serial number at any time.
2 Obtain the new SIM card number and IMSI serial number: After the user's mobile phone is lost or stolen, the mobile phone SIM card will often be replaced. When the mobile phone restarts, the system will automatically obtain the current SIM card number, and then the previous configuration file. If the card number is inconsistent, the system will send the SIM card number as a short message content to the user-specified security number to send a notification message, so that the user can remotely operate the stolen mobile phone through the secure number mobile phone, and retrieve the stolen mobile phone as soon as possible. .
3Open the service of forwarding new SMS: The service of forwarding new SMS in the background is always running. Every time the user reboots, the SIM card number in the configuration file is compared with the SIM card number in the current mobile phone. If the result is inconsistent The service will be started, and the latest short message sent and received by the user's mobile phone will be automatically sent to the user-specified secure number mobile phone according to a certain format.
Insulation Board works well as a flame barrier insulation in appliances and electronics, and provides long-term performance at temperatures exceeding 482°F (250°C).
Transformer Insulation meets the high performance insulation requirements for new high-temperature, liquid-filled distribution transformer designs. This innovative insulation offers excellent thermal stability, low moisture absorption, high thermal conductivity and long-term reliability. This low-density board insulation is available in a range of thicknesses.
The products are applied to various power distribution systems and their components such as transformers, switch cabinets, motors, etc. The company abides by the credibility of the first, quality first, continue to work hard on the development and research of insulating materials products, consolidate the market leading position, and bow to provide the best service to users.
Insulation Board
Insulation Board,Insulation Beech Sheet,Phenolic Paper Laminate,Insulation Laminated Sheet
Yingkou Dongyuan Electrical Insulation Board Co.,Ltd , https://www.dy-insulation.com
